
There remains to be tons of work to be finished with 1wallet, and I really sit up for dealing with developers In this particular Group to produce 1wallet superior. We've a huge enhance coming in over the following two months to enable several crucial characteristics and make 1wallet 100% quicker. 1wallet presently supports copyright integration and it has crafted-in integrations with applications for instance SushiSwap, Gnosis Harmless, also referred to as Harmony Multisig, and daVinci NFT marketplaces. In excess of the subsequent several months. We are going to start far more applications, indigenous consumers, and make integrations as easy as calling the regular web3 library or by only one-line of code.
In this post, we introduce some insights into accurately whom the copyright viewers is product of in an attempt to assist copyright companies learn a little bit more about the customers They're attempting to entice to their Web site, and in the end, their item.
Wyre does not aid buying 1 at this time. It is possible to get ETH then swap into A single through bridge. Having said that, the method is more intricate and expensive.
User can incorporate by moonpay but cant withdraw from the identical channel, they have got to transfer it to an exchange to withdraw
Exploit the potentialities of your respective Apple Wallet® - you don’t even have to search for the card within your apple iphone® or Apple Check out® since it is obtainable in display screen lock when you are inside the vicinity of the shop.
Impacts for the 1st many million users can come in the shape of primary money, preset-amount savings, and curated superior-produce investments. Blockchain projects are definitely the epicenter of innovations on finance and marketplaces, drawing in enormous financial commitment and returns; blockchain networks are worthwhile stakers for transaction validations and platform stability, handing out in excess of 10% annual return; blockchain lending products and solutions are facilitating billion dollars of liquidity each month, some liquidity swimming pools satisfying greater than twenty% in short-phrase returns.
สอนวิธี สมัครสล็อตวอเลท เครดิตฟรี รับได้ที่นี้!!
Proscribing customers to acquire or market specific stocks/copyright at selected times is a big purple flag, which other platforms do not
Customarily in copyright if an individual has entry to your non-public crucial they are able to acquire almost everything you personal. It can be recreation over. That is why individuals check out (frequently crazy) lengths to secure it - from engraving their seed phrase to storing it inside of a nuclear bunker.
PRIVACY: None of your own details will probably be saved on our servers, the sole facts required for your development of the cardboard is transmitted in encrypted mode (HTTPS).
On normal, Absolutely everyone can create a 1wallet in underneath 10 seconds. All you'll want to do is always to open up your camera, and scan a singular QR code in your display screen. If you're now in your cellular phone, just faucet the QR code. Then, duplicate the 6-digit code with the authenticator towards the browser. That’s it. Following a couple seconds, your 1wallet will likely be all set to go.
Ensure that you setup a recovery tackle you might have มือถือ 1wallet the keys of. This can be in the situation you lose access to Google Authenticator.
As mentioned in , in a single Wallet v0.1 the authenticator simply cannot supply safety security If your client is compromised. A compromised consumer usually means the information stored within the shopper is leaked to your malicious 3rd-occasion.
, 08/01/2018 Exactly what I had been seeking! This application is quite simple, simple application meant to incorporate your loyalty cards, tickets and passes instantly into your apple wallet. Ideal for my requires because I’m presently working with apple wallet for other loyalty playing cards.
When the attacker manipulates the method and will get your components to indicator a manipulated transaction, all of your property can equally be stolen in one transaction. Or, the attacker can just obtain the personal crucial through the hardware, In case the components is not really protected plenty of.
 Jennifer Grey Then & Now!
Jennifer Grey Then & Now! Patrick Renna Then & Now!
Patrick Renna Then & Now! Mike Vitar Then & Now!
Mike Vitar Then & Now!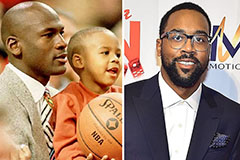 Marcus Jordan Then & Now!
Marcus Jordan Then & Now! Lucy Lawless Then & Now!
Lucy Lawless Then & Now!